Last week I joined the OpenSearch Team at AWS, a community-driven, open source fork of Elasticsearch and Kibana (read more about it here).
Security is always our top priority at AWS, so I had to learn some new development best practices in this area. One of my colleagues, and Apache contributor @nknize has been signing his commits with GPG. I decided to add my work e-mail address to my existing GPG key, and setup git signing as well.
Generating Keys
If you don’t already have a key, install gpg2 (e.g. brew install gpg), and follow the instructions in this doc. It will tell you to run gpg --full-generate-key.
You can list keys with gpg --list-secret-keys --keyid-format LONG and note the key ID.
gpg --list-secret-keys --keyid-format LONG
/Users/dblock/.gnupg/pubring.kbx
--------------------------------
sec rsa2048/75BF031B7C94E183 2013-12-24 [SC]
4A720FE790B07A68744E371675BF031B7C94E183
uid [ultimate] Daniel Doubrovkine <dblock[at]dblock.org>
In my example the key ID is 75BF031B7C94E183.
Backing up Keys
I export and store a copy of my GPG keys in Dropbox and store the private key passphrase in 1Password. The latter is required to export or import a private key (gpg will prompt you).
gpg --export-secret-key 75BF031B7C94E183 > 75BF031B7C94E183.gpg
Adding my Work E-Mail
I only have one identity, but multiple e-mails. I decided to add my work e-mail to my GPG key (YMMV) as explained here.
gpg --edit-key 75BF031B7C94E183
$ gpg> adduid
# follow prompts, finish with `save`
My key now has both my personal and work e-mail addresses.
$ gpg --list-secret-keys --keyid-format LONG
/Users/dblock/.gnupg/pubring.kbx
--------------------------------
sec rsa2048/75BF031B7C94E183 2013-12-24 [SC]
4A720FE790B07A68744E371675BF031B7C94E183
uid [ultimate] Daniel Doubrovkine <dblock[at]amazon.com>
uid [ultimate] Daniel Doubrovkine <dblock[at]dblock.org>
ssb rsa2048/960955779E55310A 2013-12-24 [E]
I then exported the public key with gpg -a --export 3AA5C34371567BD2 and added it to my Github account.
Signing Git Commits
I wanted to enable commit signing globally to avoid having to constantly appenad -S to git commit, and added the following settings to my dotfiles.
# make GPG work
export GPG_TTY=$(tty)
# use my key to sign all commits
git config --global user.signingkey 75BF031B7C94E183
# automatically sign all commits
git config --global commit.gpgsign true
Checking it Out
Commit signatures appear in git log --show-signature.
~/source/dotfiles (master)$ git log --show-signature -1
commit 073adde3335182ce33625951c84a8431adea8256 (HEAD -> master, origin/master, origin/HEAD)
gpg: Signature made Thu Apr 15 18:19:41 2021 EDT
gpg: using RSA key 4A720FE790B07A68744E371675BF031B7C94E183
gpg: Good signature from "Daniel Doubrovkine <dblock[at]amazon.com>" [ultimate]
gpg: aka "Daniel Doubrovkine <dblock[at]dblock.org>" [ultimate]
Author: dblock <dblock[at]amazon.com>
Date: Thu Apr 15 18:19:41 2021 -0400
Installing GPG keys.
And you can see a nice icon next to verified commits on GitHub!
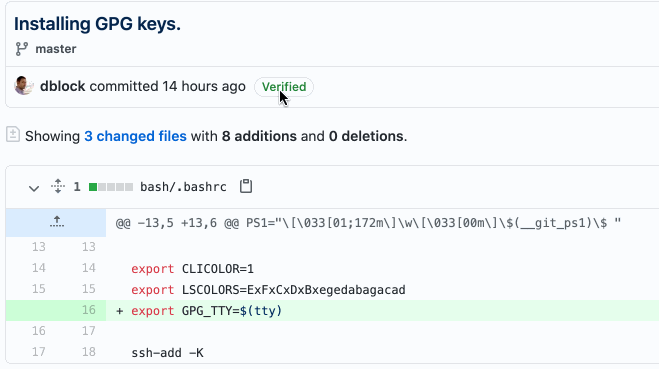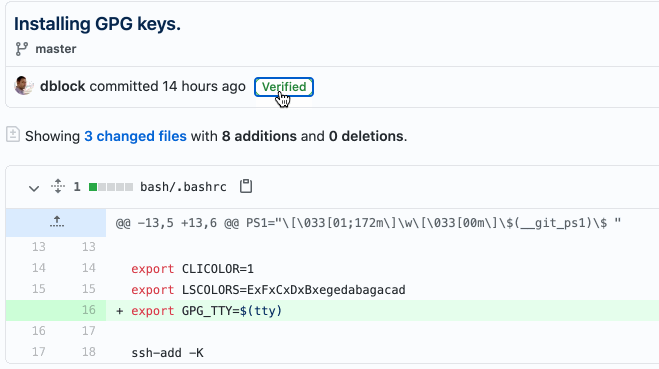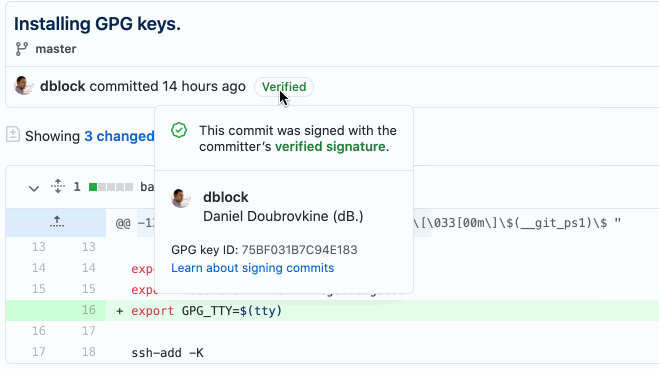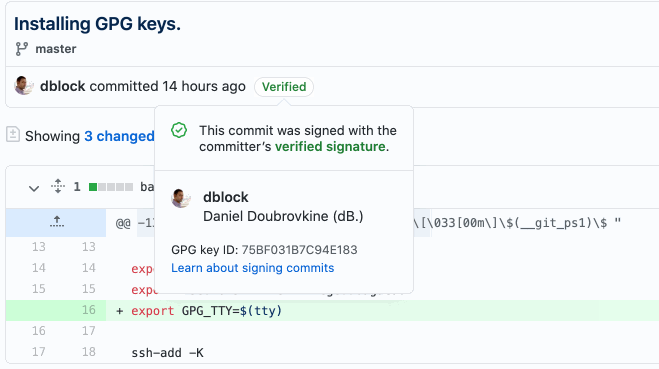
Now, how do I get verified on Twitter?!
Passphrase
I find it annoying to have to re-enter the passphrase every few minutes. Put the following into ~/.gnupg/gpg-agent.conf to set the timeout to a day’s worth.
default-cache-ttl 86400
Restart gpgagent with gpgconf --kill gpg-agent.
New Computer
Import the key on a new computer.
gpg --import ~/Dropbox/Personal/7C94E183.gpg
gpg --import-ownertrust < ~/Dropbox/Personal/7C94E183.trustlevel.txt
git config --global user.signingkey 75BF031B7C94E183
git config --global commit.gpgsign true
If you get an error gpg: no valid OpenPGP data found. and gpg: Total number processed: 0, this is a very obtuse way for GPG to tell you the that contents of the file you’re trying to import is invalid. In my case gpg --import ~/Dropbox/Personal/7C94E183.gpg was failing because the file was not synced to my local drive from Dropbox.
Troubleshooting
If you’re having trouble with gog, try echo "test" | gpg --clearsign to get a better error. If it complains that gpg-agent is not started, run gpgagent and correct any errors.

